Contributed by WTI as part of Check Point’s CPX silver-level partner sponsorship opportunity. WTI is an industry leader in out-of-band network management.
Nobody has time to drive to a site when an ISP drops service or you simply need to reconfigure and/or reboot a switch, router or firewall. Your time is too valuable not to have an out-of-band solution in place. WTI out-of-band solutions comes with a cellular connect and fallback option that gives you secure remote access to console ports as well as control of individual power outlets when your network services are disrupted.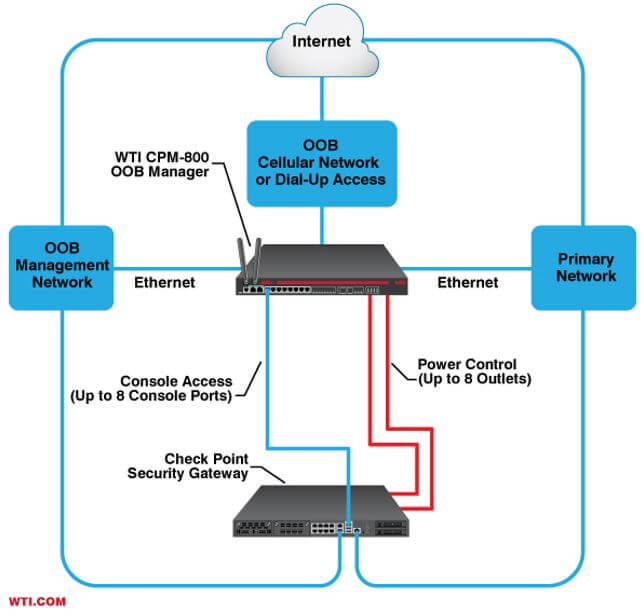
WTI out-of-band management solutions
WTI engineers and manufactures secure out-of-band management solutions for local and globally deployed networks. WTI out-of-band products are designed to ensure uninterrupted access to network devices and services by providing solutions to quickly and effectively respond to problems at distant or hard to reach equipment sites. When a router, switch or security appliance becomes inaccessible and interrupts network services, WTI out-of-band solutions provide redundant, remote console port management and power switching/reboot control to regain access and restore services in mission critical applications.
Even when the network is down, WTI out-of-band console server solutions can provide secure connectivity over primary and secondary ethernet and cellular LTE connections, allowing remote access to console ports and power control functions.
In addition, WTI DevOps allows administrators to configure, deploy and orchestrate WTI out-of-band management solutions across your entire network for automated provisioning, monitoring and disaster recovery of critical infrastructure. Features such as RESTful API, Ansible Playbooks and Python Scripting are supported.
Check Point Software Technologies and WTI
WTI offers a comprehensive out-of-band management strategy for Check Point Security Gateways, allowing your NOC to deal with equipment outages and resulting interruptions of network communication without the need to dispatch support teams to remote branch offices and data centers.
During network outages, WTI’s console server products allow you to establish remote out-of-band connections to console ports on security gateways via secure, authenticated communication protocols. If a reboot is needed, WTI Switched PDU products can provide remote out-of-band access to power switching functions at distant equipment sites. WTI also offers a combination console server plus switched PDU unit for applications that require both out-of-band console access and power reboot control.
WTI out-of-band centralized management provides access and control for all of your network devices, allowing for console data from multiple Check Point devices spread over a global network to be monitored, logged and available to administrators, simplifying the challenge of managing a large number of remote devices while minimizing resources.
With multiple connectivity options, WTI console servers including 4G LTE and/or dual Gigabit Ethernet ports can provide secure access to advanced DNS functions when primary and/or secondary ISP connections are switched or disconnected. WTI’s dual ethernet console servers allow you to remotely configure primary and secondary DNS settings and set up IP tables to maximize availability of security gateways during network outages, ensuring seamless transfers between primary and secondary ISPs. The optional 4G LTE internal modem provides a secure additional alternate path for out-of-band connectivity using security protocols such as IPSec and OpenVPN.
About WTI
WTI designs and manufactures Secure Out-of-Band Management Solutions for local and globally deployed networks. WTI provides redundant OOB console access and power control to mission critical infrastructure … even when the network is down. WTI products can be purchased factory direct and through various channel partners worldwide. Since 1964, WTI has maintained local in-house manufacturing, engineering and technical support. Learn more at www.wti.com.
About Check Point Software Technologies, Ltd.
Check Point Software Technologies Ltd. (www.checkpoint.com) is a leading AI-powered, cloud-delivered cyber security platform provider protecting over 100,000 organizations worldwide. Check Point leverages the power of AI everywhere to enhance cyber security efficiency and accuracy through its Infinity Platform, with industry-leading catch rates enabling proactive threat anticipation and smarter, faster response times. The comprehensive platform includes cloud-delivered technologies consisting of Check Point Harmony to secure the workspace, Check Point CloudGuard to secure the cloud, Check Point Quantum to secure the network, and Check Point Infinity Core Services for collaborative security operations and services.
WTI out-of-band management solutions provide Check Point security gateways with:
- In-band and out-of-band console access from anywhere.
- Remotely reconfigure, revive and restore gateways via SSH.
- Connect via ethernet or cellular 4G LTE with optional failover.
- Power cycle and monitoring capabilities.
- Faster network issue resolution.
Application example
Challenge: Provide secure, authenticated access to configuration parameters on console ports on Check Point security gateways during outages.
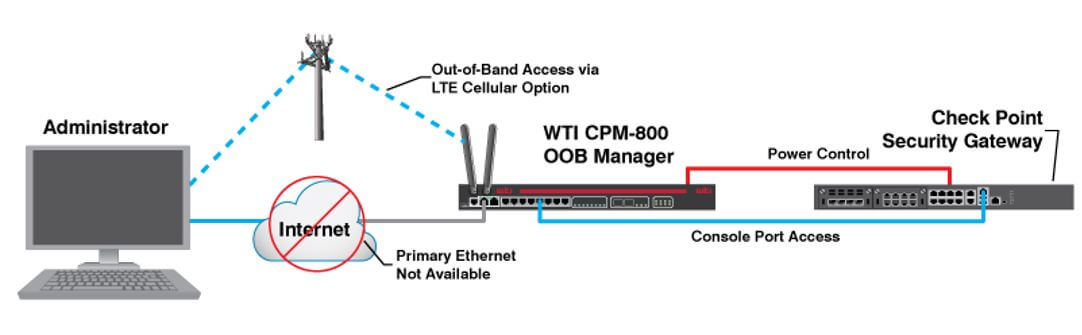
Answer: WTI console servers with dual gig ethernet ports ensure secure console port connections via primary and secondary ethernet as well as OOB access via optional LTE cellular modem.
Results: If the primary in-band network fails, admins can initiate secure SSH connections to security gateway console ports via out-of-band, allowing access to configuration parameters and other data used to troubleshoot unresponsive devices and revive network services.
In conclusion, WTI out-of-band management solutions empower your team to regain control quickly and reduce network disruptions. Are you ready to save time, energy and resources? Let’s discuss how WTI can help!