A University of Alberta researcher is awarded $748,500 from Alberta Innovates to test a new portable ultrasound system that…
Ukrainian Drones Destroyed Yet Another T-54: Why Are These Tanks Still a Thing for Russian Army? – Technology Org
Name a few current main battle tanks of the Russian forces. If you know anything about armoured vehicles…
Unicorn Overlord Review – Tactical Superiority – Game Informer

Draw from enough unique inspirations, and eventually, a game begins to feel entirely novel. That’s the sensation that emerges as you play Unicorn Overlord, Vanillaware’s vast fantasy adventure of tactics, strategy, and storytelling. I was consistently reminded of other systems and mechanics from prior genre releases, but the resulting combination felt consistently original and entertaining, even after many hours of battle and exploration.
Players control a young, exiled prince in a high fantasy world as he gradually gathers an army to take down an all-powerful empire. There’s a significant focus on story and character development from beginning to end. The fact that the plentiful “thees and thous” frame an especially trope-heavy and familiar plot doesn’t diminish the enjoyment. Instead, I was delighted by the confident and well-written dialogue and its willingness to embrace the fun of countless long-lost siblings, figures in disguise, and redemptive character arcs. By the end, some interesting choices let you shape the game’s outcome, but this isn’t a game of bold narrative surprises – simply well-told comfort-food fantasy antics.
Unicorn Overlord is awash in systems that govern your army’s advancement and improvement. Whether it’s equipment, honor, renown, gold, or character level, the primary goal is growing your army, promoting your combatants, expanding the potential size of each unit, and setting up a team that can triumph in the field. Everything works together admirably, and it’s great fun to tweak each small squad unit to create unstoppable combos of damage, defense, and healing.
Battles are an intriguing mix of real-time troop movement and small unit-to-unit skirmishes. By adjusting each character’s formation placement and tactical decision-making before a melee, you set them up for success. However, once an exchange begins, your role as commander is in the back seat; you can’t affect the outcome anymore – only watch as it plays out. As such, much of the gameplay is about clever unit placement, movement, use of items, and pre-battle powers. I enjoyed overseeing a large and diverse army of knights, witches, gryphon riders, and elven archers as they strode into a righteous rebellion.
[embedded content]
Vanillaware’s attention to detail and high production value are on full display. The vast top-down overworld is stacked with detail and vibrant, illustrated backdrops. The score is grand and dramatic, accompanied by a tremendous bounty of memorable voice acting. Most notably, both story moments and unit battles unfold featuring the studio’s striking trademark art and animation style, which leverages exaggerated deformation of everything from weapons to character curves and musculature to accentuate the fantasy setting and tone.
While I consistently enjoyed my dozens of hours with Unicorn Overlord, the latter half of the game begins to show some cracks in the fun. Because you can preview the outcome of each battle (which is good), many players will eventually do what I did, and begin to skip the bombastic visuals of a given skirmish to get on with the larger battle. The thrill of those lavishly illustrated scenes sadly begins to lean toward tedium.
Likewise, the plentiful unit types you both recruit and face in battle are initially intriguing but eventually become extremely challenging to keep straight. Imagine a game of “Rock, Paper, Scissors” where you can throw any one of dozens of distinct hand signs, and you can see the dilemma. Tactical complexity is good, but I ultimately found keeping all the distinctions straight slowed down the pacing and sense of mastery rather than enhancing an already rich tactical simulation. Combine those two problems, and late-game battles can feel repetitive and muddled.
Even acknowledging those frustrations, I love the variety of encounters Unicorn Overlord presents and the seamless way so many interlocking game systems contribute to an overarching saga of magic and warfare. From beginning to end, the game feels crafted, balanced, and deep, without sacrificing approachability. Set aside preconceptions from the unusual name, and you’ll find an epic well worth exploring.
Transformative Trends: GenAI & Hyperautomation Propel Organizations into a New Era of Success
Organizations are under constant pressure to innovate. Embracing innovation allows companies to develop new products, services, and processes, crucial for maintaining a competitive edge. As companies strive to meet the demands of their customers and anticipate industry disruptions, embracing GenAI and hyperautomation becomes imperative for maintaining…
The AV-over-IP Revolution is Happening NOW! – Videoguys

Explore the dynamic world of AV-over-IP (AVoIP) technology in this insightful blog post by Dan Ferrisi. Discover the driving forces behind the surge in AVoIP adoption within the audiovisual integration landscape and gain valuable insights into market trends and expert perspectives.
Market Penetration of AVoIP: Delve into exclusive data from Commercial Integrator’s research study as we uncover the market penetration of AVoIP solutions. Learn about the varying utilization rates among integrators and the factors influencing AVoIP adoption. Explore the pivotal role of AV/IT convergence in shaping industry dynamics.
Expert Perspectives: Benefit from the wisdom of industry leaders as we present thought-provoking insights from technology experts like Sean Wargo of AVIXA and Marty Fornelli of Diversified. Gain valuable perspectives on AVoIP’s current landscape and future trajectory from these seasoned professionals.
Powering AVoIP’s Ascent: Explore the driving forces behind AVoIP’s relentless ascent, from pioneering integrators to innovative hardware manufacturers. Learn how these key players are shaping the future of AVoIP technology.
Vertical Markets and Applications: Discover the versatility of AVoIP technology across diverse verticals and applications, from corporate environments to educational institutions. Explore compelling use cases where AVoIP solutions offer unparalleled advantages.
Benefits of AVoIP: Uncover the myriad benefits of embracing AVoIP technology, including streamlined cabling infrastructure, enhanced efficiency, and scalability. Learn how AVoIP solutions revolutionize audiovisual systems while delivering cost-effective and future-proof solutions.
Current Concerns and Future Outlook: Address lingering concerns surrounding network security, skillset requirements, and the proliferation of AVoIP standards and protocols. Gain insights into the challenges and opportunities shaping the future of AVoIP technology.
Join Dan Ferrisi on a journey through the AV-over-IP revolution and envision the future of audiovisual integration. With expert insights and market analysis, discover the transformative potential of AVoIP technology and its impact on the digital collaboration landscape.
Read the full article by Dan Ferrisi for Commercial Integrator HERE
A primer on MESH networks and MESH cyber security – CyberTalk

Gergana Kungalova is a Security Engineer for Check Point in Bulgaria. She started her journey in the Cyber Security field as Network Security Support Engineer, working with customers across the globe. In her current role, she is connecting people and processes with technology by matching the clients’ business needs with security solutions and services.
In this amazing expert interview, Gergana Kungalova explains why MESH networks can be more advantageous than traditional networks, she addresses common misperceptions around MESH, and then highlights MESH-specific cyber security measures. Don’t miss this!
What is the core idea behind MESH networks?
The MESH network provides ultimate connectivity between nodes like users, servers/applications, and network components. The main driver for this architecture is to provide reliable access that is not dependent on a single device or route.
Why might an organization choose to have a MESH network over traditional network architecture?
The traditional network architecture was suitable for organizations when they had well-defined perimeters and point-to-point connections. All services were hosted within the data centers and users were working strictly from the office. Nowadays, the demand for mobility and scalability has completely changed the picture. We have services that are hosted in the cloud and/or in the data center. At the same time, our users are roaming and should access these services from everywhere. The new connectivity requirements have increased the complexity of managing networks and security to an extreme degree. Many organizations are choosing the MESH networks as an enabler for flexible and scalable infrastructure. It allows them to reduce the management overhead and cut costs.
What are some common misperceptions about MESH that we should debunk for readers, if any?
The most common misperception is that the MESH networks are more secure. They are more agile and resilient, but they introduce new dynamics in the monitoring and the maintenance which may pose risk of security breach. The nature of MESH networks may increase the amount of time required for identifying breaches, determining which nodes have been affected and what the business impact looks like. Also, the root cause analysis is more complex and time consuming.
It is critical to implement cyber security measures at every point of the infrastructure, in the early stages. The security must be multi-layered and part of the planning phase. A cyber security platform that is consolidated and focused on prevention is the best approach to ensure business continuity within organizations with MESH networks.
Examples of typical cyber security threats seen on MESH networks?
The cyber security threats seen on MESH networks are the same as the threats seen on the traditional networks – vulnerability exploits, phishing attacks, account takeover…etc. The only difference is how they are executed.
How does the decentralized nature of MESH networks impact the design and implementation of robust cyber security measures?
The dynamic nature of MESH networks requires multi-layered enforcement of cyber security. The best-of-breed method is bringing more complexity then benefits – multiple management consoles, no full visibility on security posture, lack of expertise…etc. To address these challenges, we should talk about the concept of Cyber Security Mesh Architecture (CSMA)*.
The CSMA approach focuses on platform security that is collaborative across all components in the customer’s environment and it’s built on the following pillars: Security Analytics and Intelligence, Distributed Identity Fabric, Consolidated Privacy and Posture Management, and Consolidated Dashboards. It means that all security components talk with each other, share intelligence and have one single pane of glass for management. The efficient implementation of CSMA has to be enforced based on user identity and zero trust principals, not on network-based access.
*“CSMA is a concept developed by Gartner to help companies move past siloed security to a more collaborative and flexible approach to security. CSMA is designed to make security more composable and scalable by modularizing security functions and enabling them to interoperate through a set of supportive layers. By making security more cohesive and collaborative, CSMA enables an organization to achieve better security with fewer resources.” — Quoted from Check Point’s What is Cybersecurity Mesh Architecture (CSMA)?
Given the potential for node compromise in MESH networks, what strategies can be employed to enhance the security posture of individual nodes, as to prevent cascading security issues across the network?
In case of compromise, the time spent for identification and mitigation is what really matters, as does determining how big the impact on the business will be. The prevention first methodology has to be incorporated into the cyber security strategy. From my experience, it does not matter as to how many security measures are in place – they have to be configured in prevention mode in order to block the attack. Of course, to cover all possible threat vectors, we should have in place strong encryption, zero-day prevention, anti-phishing, anti-ransomware, vulnerability, and patch management.
What other kinds of tools or technologies can cyber leaders use to monitor for suspicious activities within a MESH network?
Cyber leaders can benefit from integrated AI engines:
- AI integrated within the prevention engines can reduce the time for mitigation, improve catch rate and discover attacks chains in next to no time.
- AI integrated in the monitoring can improve behavior analysis and discover anomalies, provide sophisticated reports, and reduce the time for root cause analysis.
An example of a technology that combines both is MDR/MPR (Managed Detection/Prevention and Respond). It can provide a deeper overview of what is going on in the environment and help to further decrease the reaction time. Basically, it’s providing automation and optimization for how the SOC teams are working with data and dangerous threats.
Is there anything else that you would like to share with the Cyber Talk CxO audience?
Cyber security requires a continuous process of risk management and effectiveness optimization. Building robust architecture requires approach that is collaborative, redistributed within all parts of the environment and focused on prevention.
Stay (cyber) safe 🙂
AI safety is not a model property
Trying to make an AI model that can’t be misused is like trying to make a computer that can’t be used for bad things…
Final Fantasy X’s Theme Song ‘To Zanarkand’ Wasn’t Originally Intended For The Game
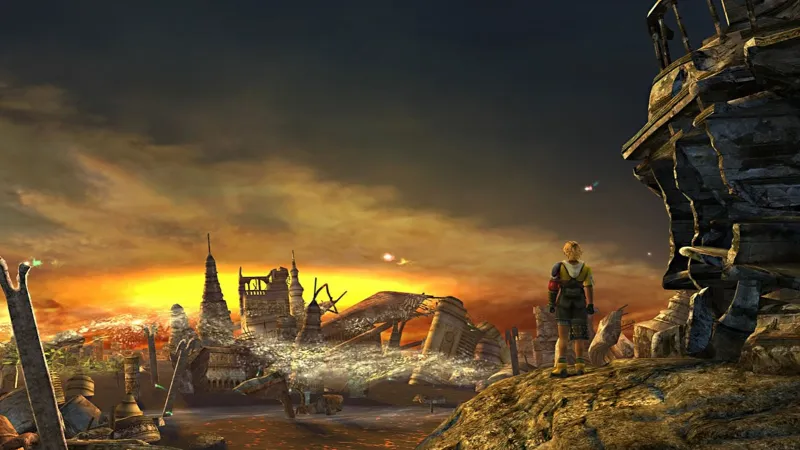
If you ask any Final Fantasy fan what their top five favorite songs in the franchise are, there’s a 99 percent chance one of them is “To Zanarkand” from Final Fantasy X. However, it turns out, it wasn’t originally intended for the game.
This news comes from Audrey (aitaikimochi on X, formerly Twitter), a mega Final Fantasy fan, Twitch streamer, and CEO of Aitai Japan Inc., who translated a recent interview between Weekly Ochiai and Final Fantasy X composer Nobuo Uematsu, whose credits also include One-Winged Angel and Aerith’s Theme from Final Fantasy VII and so much more. In that interview, Uematsu revealed “To Zanarkand” originally began as a piece for a French flute player, meant to be played during a recital.
[embedded content]
“‘To Zanarkand’ was actually not meant to be the theme for Final Fantasy X,” Uematsu tells Weekly Ochiai, as translated by Audrey on X. “There was a flute player from France who originally asked me to write a song for them to play during a recital. When I wrote the piece, I thought perhaps this sounded a bit too sad for a recital. So I set it aside for the time being.
“Sometime after, when I was making the score of Final Fantasy X, I was falling behind all the while the producers were hounding me. So since that flute piece was unused, I just kind of meekly handed it to them. They listened to it and said, ‘Yes! This is brilliant!'”
In retrospect, it’s wild “To Zanarkand” wasn’t originally composed by Uematsu for Final Fantasy X because it fits the game’s themes so well, nailing the somber and sad tone present throughout Tidus and Yuna’s journey in Spira.
For more about Final Fantasy music, read Game Informer’s exclusive four-part series on composer Masayoshi Soken’s score for last year’s Final Fantasy XVI:
After that, read Game Informer’s review of Final Fantasy X/X-2 HD Remaster.
What’s your favorite Final Fantasy theme song? Let us know in the comments below!
