There are AI optimists and AI pessimists, but what everyone agrees on is that AI will be transformative. From generating ideas for screenwriters to crunching vast amounts of data for analysts, it has countless diverse uses. But what will it mean for the events industry? Event…
New Assistive Robot Combats Mild Cognitive Impairment
Researchers at the University of California – San Diego have introduced CARMEN, a Cognitively Assistive Robot for Motivation and Neurorehabilitation, designed to address the growing challenge of Mild Cognitive Impairment (MCI) in older adults. MCI affects approximately 20% of individuals over 65, serving as a potential…
“If” CSS Gets Inline Conditionals
A few sirens went off a couple of weeks ago when the CSS Working Group (CSSWG) resolved to add an if() conditional to the CSS Values Module Level 5 specification. It was Lea Verou’s X post that same day that …
“If” CSS Gets Inline Conditionals originally…
Transforming network security | Three ways AI can boost infrastructure operations – CyberTalk
By Ulrica de Fort-Menares, Vice President of Product Management for Infrastructure Assurance at BlueCat Networks
Artificial intelligence (AI) has the power to reshape how you operate your network security infrastructure.
Firewalls have been a first line of defense in network security for many years and must always be operational. Maintaining five nines, or service availability 99.999% of the time, requires skilled network security practitioners. However, many enterprises have a limited number of security experts and struggle to find enough skilled expertise to manage their increasingly complex network infrastructure.
An AI-powered, knowledge-based expert system can expand team skills so that they’re available around the clock and can help your enterprise more easily manage highly complex network security infrastructure.
In this article, we’ll explore three ways that AI can boost your network security operations and augment limited resources. Specifically, we’ll look at how you can:
- Use a knowledge-based expert system to find hidden issues in your security infrastructure before they become bigger problems
- Combine that system with automation to automatically troubleshoot complex problems, much like a human would
- Utilize machine learning models to detect anomalies in an enterprise environment
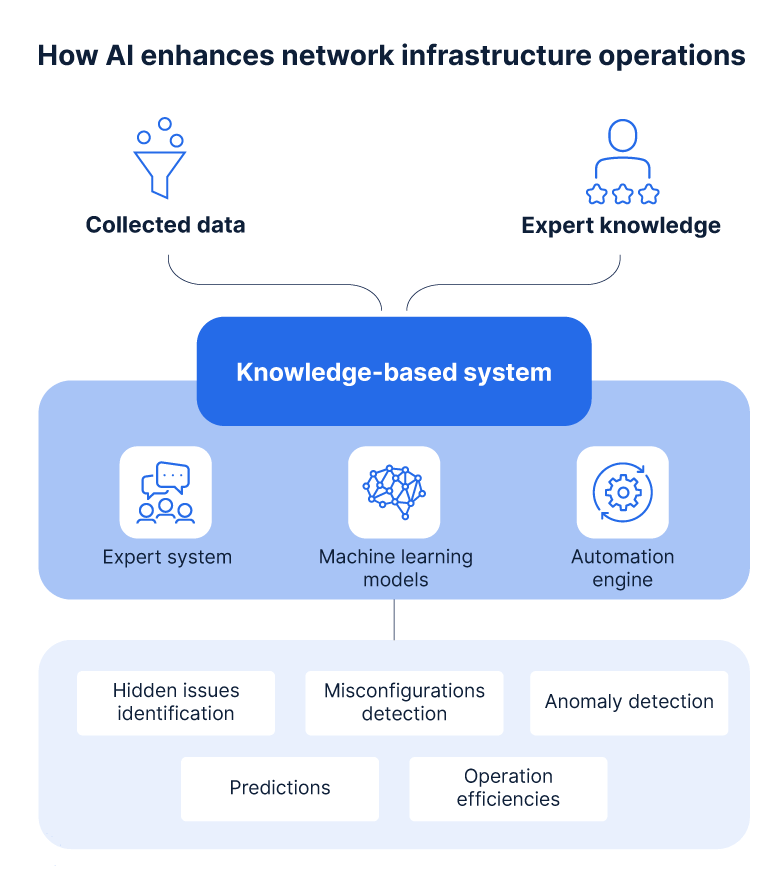
Find hidden issues with a knowledge-based expert system
A knowledge-based system is a form of AI that encodes the collected knowledge of human experts to detect and solve difficult problems. Knowledge-based systems generally consist of a data repository or knowledge base, an inference or rules engine to locate and process data, and a user interface. Knowledge-based systems can assist with expert decision-making, easily process large quantities of data, and reveal insights or create new knowledge from existing information.
When applied to network security, a knowledge-based system contains in-depth knowledge, culled from human experts’ technical practices and experiences, of how security infrastructure should work and behave. Like a firewall engineer, it can analyze data, detect issues, and prioritize alerts, just with much greater speed and at a much larger scale than what a human is capable of. A system based on the knowledge of human experts can assist with identifying problems and can help network security teams troubleshoot technical issues. It can augment team skills, allowing teams to do more with less.
Let’s look at a specific example of a network security application:
A knowledge-based system can know how important a Border Gateway Protocol (BGP) peer is to route traffic to the internet and that detecting BGP issues is more than just monitoring the peer state. It can also ensure that the routing process learns routes from its BGP peer and passes the information to the secure gateway’s routing table. Further, it can alert you the moment it detects a hidden route condition.
Another benefit of a knowledge-based system is its sophisticated rule engine, which can detect complex problems. Building on the same BGP example, the system has knowledge about a clustered environment. If the passive member of the cluster does not have any active routes, it is OK. But if the active member of the cluster has zero active routes, it is not OK. The system operates on more than just a simple if-then-else construct.
Auto-triage with a knowledge-based expert system
Perhaps one of the most important uses of AI is to help us automate tasks. By coupling a knowledge-based expert system with an automation engine, we can perform automated troubleshooting. The system applies a broad base of domain-specific expertise and makes intelligent decisions about the situation. Much like a human would, it walks down a decision tree to diagnose a complex problem.
Let’s explore this further using the example of a BGP peer going down. The system runs investigative steps. It follows a troubleshooting workflow with branches gathered from industry experts and fed into the system. Applying domain knowledge is key to determining what relevant information to analyze.
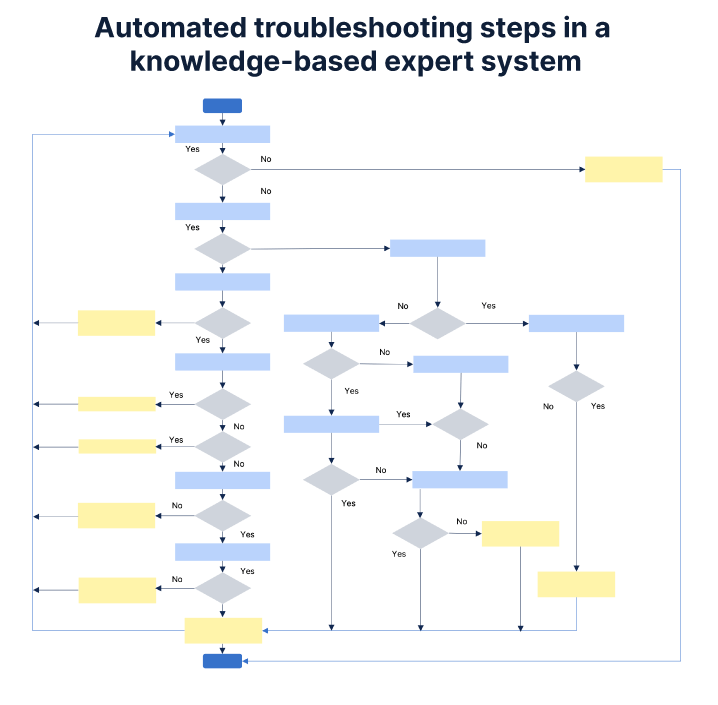
In this example, multiple conditions and scenarios are considered, as the troubleshooting steps have different branches based on the configuration. The steps to troubleshoot a Layer 2 BGP connectivity issue are very different from one in Layer 3. As you can see from this workflow, troubleshooting a down BGP peer isn’t exactly a straightforward task.
Using a knowledge-based expert system to automatically diagnose a problem augments IT teams and improves mean time to resolution.
Detect anomalies with machine learning models
Any nuances in the operational conditions of security infrastructure can signal unacceptable levels of business risk. Therefore, anomaly detection is an important tool for identifying rare events or outliers that may be significant.
For example, if a firewall is receiving a sudden increase in “non-syn-tcp” first packets, it may be indicative of an asymmetric routing issue in the network environment. The ability to detect these rare conditions or outliers can avoid bigger problems.
While machine learning is one of many kinds of AI, it is typically most used for detecting anomalies. One of the simplest and oldest ways to detect anomalies is to use statistical methods, such as standard deviation or z-score. However, these methods have some limitations, such as being sensitive to outliers, assuming a fixed distribution, and not capturing complex patterns in the data.

In this chart, we are looking at the number of concurrent connections over four months. A human can easily identify the three outliers, but a machine needs to be trained. The outliers are:
- A dramatic increase in the number of connection counts in late October
- A similar increase in the middle of November
- Then, a dramatic decrease of connection counts over the Christmas holidays
Deep learning for anomaly detection can apply to security infrastructure in novel ways. For example, we can examine data relating connection counts with CPU usage to find common patterns. With deep learning methods, we can provide even higher fidelity alerts around anomalies.
The autoregressive integrated moving average model is known for forecasting stock market returns. But we can leverage this algorithm and machine learning to make predictions about your security infrastructure based on historical data. For example, the system can determine at what point your device needs upgrading to support your number of concurrent connections. This can greatly simplify capacity planning.
Summary
Without automation, security teams would spend countless hours gathering diagnostics and data just to keep firewalls and other security infrastructure up and running. Still, a typical security engineer can spend a notable portion of their time identifying and remediating known errors. Security teams often have limited resources, resulting in an even greater need for automated diagnostics and issue detection.
With an AI-powered solution, you can leverage machine learning models and a knowledge-based expert system to detect potential issues before they become bigger problems and troubleshoot these anomalies in your environment like a human would. And it can serve up recommended remediations that security engineers would otherwise have to find and implement manually.
While its capabilities are relatively nascent, even today’s AI has the power to transform the way you operate your network security infrastructure.
How Wealth Managers Can Build Trust Through the Power of Automation and AI
Building trust between wealth managers and their clients has traditionally been credited to effective communication and understanding between the two partners. Over time, wealth managers’ have become increasingly spread thin because of larger portfolios of more demanding clients. The knock-on effect is that clients can feel…
MARKLLM: An Open-Source Toolkit for LLM Watermarking
LLM watermarking, which integrates imperceptible yet detectable signals within model outputs to identify text generated by LLMs, is vital for preventing the misuse of large language models. These watermarking techniques are mainly divided into two categories: the KGW Family and the Christ Family. The KGW Family…
Pioneering Open Models: Nvidia, Alibaba, and Stability AI Transforming the AI Landscape
Artificial intelligence (AI) is profoundly transforming the world, and innovative companies like Nvidia, Alibaba, and Stability AI are among the leaders of this transformation. These companies are making advanced models accessible to a broader audience, advancing innovation, promoting transparency, and enabling diverse applications across industries. This…
Vizrt CaptureCast Saves the Day – Videoguys

The article titled “Class of 2024: University of Utah, SJ Quinney College of Law” by Macy O’Hearn for AVNetwork, discusses how the University of Utah’s SJ Quinney College of Law cost-effectively expanded the availability of their lecture capture (LC) service to more classroom locations. The college invested in an NDI-based LC solution from Vizrt called CaptureCast, which can consume the growing number of NDI-based sources added to the learning spaces using both software and hardware NDI solutions. The main challenge was gaining traction and support for the AVoIP (specifically NDI) solutions from the central campus resources, as the college needed resources not available on staff, with AV system coding support being the most critical need to enable coding the legacy matrix switch out of the equation and adding support for the NDI-based solutions into the existing touch panel UI.
What were the main goals of this project at the University of Utah’s SJ Quinney College of Law?
The main goals of the project at the University of Utah’s SJ Quinney College of Law were to cost-effectively continue to support established lecture capture processes and expand the availability of the lecture capture service to more classroom locations.
What was the main challenge the college faced in implementing the new lecture capture solution?
The main challenge the college faced in implementing the new lecture capture solution was gaining traction and support for AVoIP (specifically NDI) solutions from central campus resources. As a smaller department, the college needed resources not available on staff, with AV system coding support being the most critical need. This support would enable coding the legacy matrix switch out of the equation and adding support for the NDI-based solutions into the existing touch panel UI.
What equipment was used in the new lecture capture solution?
The equipment used in the new lecture capture solution at the University of Utah’s SJ Quinney College of Law included Magewell Pro Convert HDMI Plus, NewTek NDI Tools screen capture and webcam tools, and the NewTek CaptureCast Server.
Read the full article by by Macy O’Hearn for AVNetwork HERE
Learn more about Vizrt below:
SenseTime SenseNova 5.5: China’s first real-time multimodal AI model
SenseTime has unveiled SenseNova 5.5, an enhanced version of its LLM that includes SenseNova 5o—touted as China’s first real-time multimodal model. SenseNova 5o represents a leap forward in AI interaction, providing capabilities on par with GPT-4o’s streaming interaction features. This advancement allows users to engage with…
PlayStation’s PC Strategy Is Going Well As Ghost Of Tsushima Was The Best-Selling Game Of May 2024

PlayStation’s PC efforts are paying off, if the latest U.S. Video Game Market Highlights report from analyst group Circana is any indication. That’s because developer Sucker Punch Production’s Ghost of Tsushima, which originally launched on PlayStation 4 back in 2020, was the best-selling game of May 2024 in the U.S. And that’s almost assuredly due to the recent PC release of Ghost of Tsushima Director’s Cut on May 16.
Ghost of Tsushima Director’s Cut hit PC almost four years after the game’s initial launch on PS4, which speaks to PlayStation’s PC release strategy it detailed last month. It said its live-service games, like this year’s Helldivers 2 or the upcoming 5v5 hero shooter Concord, will launch day-and-date on PC, but its tentpole single-player games, like Ghost of Tsushima Director’s Cut and God of War Ragnarök (hitting PC this September), will launch at later dates.
[embedded content]
The rest of the top 10 for May 2024 looks like this:
- Ghost of Tsushima
- Paper Mario: The Thousand-Year Door
- Call of Duty: Modern Warfare III
- Helldivers II
- MLB: The Show 24
- Sea of Thieves
- Minecraft
- Elden Ring
- Hogwarts Legacy
- Stellar Blade
And here’s what the top 20 best-selling games of the entire year look like:
Year-to-Date Ending May 2024 Top 20 Best-Selling Premium Games – U.S. (Dollar Sales, Physical and Digital from digital data sharing publishers, excludes add-on content) pic.twitter.com/Wnacwg4ixw
— Mat Piscatella (@MatPiscatella) July 8, 2024
For May 2024, content spending fell 3% compared to May 2023, down to $3.6 billion, even despite a 13% growth in mobile content spending. However, that 13% increase in mobile spending was offset heavily by a 40% drop in console content spending, according to Circana executive director Mat Piscatella. He attributes the May 2024 console spending decline (compared to May 2023) to the strength of The Legend of Zelda: Tears of the Kingdom’s launch last year.
Elsehwere in the report, Piscatella says video game hardware spending declined 40% as well when compared to May 2023, down to $202 million. “Through May, all current generation hardware platforms are showing double-digit percentage declines year-on-year in 2024, with Switch showing the most significant drop,” Piscatella writes on X (formerly Twitter).
The PlayStation 5 led May 2024’s hardware market in unit and dollar sales, with the Switch in second for unit sales and the Xbox Series X/S in second for dollar sales. Throughout each console’s 43 months on the market, the PS5 is up by 8% compared to the PS4 and the Xbox Series X/S is down 13% compared to the Xbox One.
May spending on video game accessories dropped 8% when comparing May 2024 to May of last year, and the PlayStation Portal was the best-selling accessory in dollar sales for the month – it’s also the best-selling accessory for the entire year.
For more, be sure to check out the entire Circana report here. After that, read Game Informer’s Ghost of Tsushima review, and then check out this video for a look at how Ghost of Tsushima Director’s Cut runs on Steam Deck.
Have you been playing Ghost of Tsushima Director’s Cut on PC? Let us know in the comments below!

