BlinqIO, an innovative AI-driven software testing platform, has secured $5 million in funding, led by Boston-based Flint Capital along with key Silicon Valley executives and top-tier investors, including Inovia Capital and TAL Ventures. This investment is set to drive BlinqIO’s expansion across the United States, addressing…
Apple Intelligence: Transforming Your iPhone into a True Assistant
On June 10, at the WWDC, Apple unveiled a groundbreaking revelation: the integration of artificial intelligence across all its products, headlined by the eagerly awaited iOS 18, which is usually available in September. This innovation, forged through a strategic alliance with OpenAI, promises to revolutionize Siri,…
OWC Intros Slick Powerful Storage for Content Creators – Videoguys

At Computex 2024, OWC showcased a variety of cutting-edge storage solutions for creators, as reported by btarunr for TechPowerUp. Renowned for their compatibility with Macs and iOS devices, OWC’s latest offerings are now standardized for both Macs and Windows PCs.
The OWC Thunderbolt Go Dock supports Intel’s new Thunderbolt Share standard, enabling a 40 Gbps network connection between two PCs or Macs. It facilitates sharing its ports, I/O, and card readers, including two downstream Thunderbolt 40 Gbps, HDMI display output, gigabit Ethernet, two 10 Gbps USB 3.2 Gen 2 type-A, a 10 Gbps USB 3.2 Gen 2 type-C, USB 2.0, HD audio with a 4-pole headset jack, and an SD card reader. The dock has its own internal power supply, driving all functions.
The Express 1M2 is a sleek, USB4-based portable SSD enclosure with an M.2-2280 slot featuring PCI-Express 3.0 x4 connection, achieving tested bandwidths up to 3151 MB/s. The aluminium enclosure, acting as a heatsink, supports up to 8 TB drives, starting at $249 for the 1 TB model.
OWC’s ThunderBlade X8 is a desktop portable SSD enclosure housing up to eight M.2-2242 SSDs, providing a total of 32 TB storage with RAID 0/1/4/5/1+0 configurations. In RAID 0, it offers sequential read speeds up to 2826 MB/s and write speeds up to 2949 MB/s. It features a 40 Gbps Thunderbolt 3 interface with two ports for daisy-chaining.
The Envoy Pro Elektron is the newest addition to the Envoy line, a portable SSD starting at $99.99 for the 240 GB model, and going up to 4 TB. It contains an M.2-2242 SSD with PCIe Gen 3 x2 connectivity and uses a 10 Gbps USB 3.2 Gen 2 bridge chip.
Finally, the Atlas USB4 CFexpress 4.0 Card Reader provides seamless connection to CFexpress 4.0 memory cards via a 40 Gbps USB4 interface. OWC also presented a range of SD, SDexpress, and CFexpress memory cards under the Atlas brand.
Read the full article by btarunr for TechPowerUp HERE
Stalker 2: Heart Of Chornobyl’s Latest Trailer Shows Plenty Of Gameplay

Stalker 2’s Xbox Showcase trailer was fully focused on gameplay. Monsters were shot, vendors were visited, doors were pried open, and apocalyptic locations were explored. You can check out the trailer below.
[embedded content]
Stalker 2: Heart Of Chornobyl releases September 5. For more on Stalker 2 head here.
Prince Of Persia: The Sands Of Time Remake Is Coming In 2026

Prince of Persia: The Sands Of Time reemerged during Ubisoft’s Forward event, but only slightly. Basically, Ubisoft confirmed the game is still in development, but it won’t be releasing until 2026.
The game has hit some development difficulties over to course of its creation. When announced, Ubisoft Pune and Ubisoft Mumbai were said to be developing the game, but in 2022 it was shared that development duties would be handed over to Ubisoft Montreal. It seems at that time development was effectively fully reset because it will be some time before release.
For more on Prince of Persia: The Sands of Time remake, head here. For a look at the original game, you can check out our recent episode or Replay below.
[embedded content]
An Into The Spider-Verse Costume And More Are Coming To Spider-Man 2 Later This Month
Marvel’s Spider-Man 2 is getting an update on June 18 that “addresses some community feedback and adds stability improvements to the game,” but the more exciting detail is the addition of eight new suits, one of which is in reference to the Spider-Verse films.
A suit inspired by Peter B. Parker’s look will be available for Peter Parker, seen below, although it does lack his telltale gut. The other seven suits, which can be seen on PlayStation’s blog, have been created by guest designers KidSuper, Vini Jr, Lando Norris, and Rina Sawayama. There are also a few suits referencing specific Spider-Man lore, and a new Mile Morales suit (seen above) that “is reminiscent of classic cartoons and comics of old.”

For more on the web-slinger latest video game adventure, you can read Game Informer‘s Marvel’s Spider-Man 2 review here.
Arcane Season 2, Which Will Be The Final Chapter, Gets A New Teaser Trailer Ahead Of November Premiere

Netflix had released a new trailer for Season 2 of Arcane, the hit animated series set in the League of Legends universe. Set to premiere in November, show creators Christian Linke and Alex Yee confirm the upcoming season will be the show’s last.
[embedded content]
Season 2 is billed as “the final chapter” and will center on Jinx’s attack on the Council, which will be the centerpiece of the escalating Piltover/Zaun conflict. Hailee Steinfeld (Vi) and Ella Purnell (Jinx) will reprise their roles in Season 2. While Arcane will conclude, Christian Link stated during a League of Legends dev update today that it won’t be the last animated tale based on the franchise.
“Arcane is just the beginning of our larger storytelling journey and partnership with the wonderful animation studio that is Fortiche,” said Linke. “From the very beginning, since we started working on this project, we had a very specific ending in mind, which means the story of Arcane wraps up with this second season. But Arcane is just the first of many stories that we want to tell in Runeterra.”
You can watch the first teaser for Arcane Season 2 here. For more on League of Legends, check out our in-depth preview of 2XKO, the franchise’s upcoming fighting game.
San Francisco 49ers’ Christian McCaffrey Graces Madden NFL 25 Cover

Madden NFL 25 (the new one, not the bizarrely titled 25th-anniversary entry of the same name from 2013) has found its cover athlete. Hot off his run to a near-victory in Super Bowl LVIII comes San Francisco 49er running back Christian McCaffrey.
The reigning NFL Offensive Player of the Year will grace the standard and Deluxe Editions. You can view both covers in the gallery below.
EA has yet to detail Madden 25’s gameplay but teases the next evolution of current-gen/PC exclusive features such as FieldSense, new commentary and presentation, and updates to Franchise and other modes. A press release states EA plans to announce gameplay details “soon.”
Madden NFL 25 launches on August 16 for PlayStation 5, Xbox Series X/S, PlayStation 4, Xbox One, and PC. You can read our review of last year’s Madden NFL 24 here. For the first time in years, Madden won’t be EA’s only licensed football sim this year, as EA Sports College Football makes its comeback on July 19. You can watch the first trailer here.
Talon AV’s Sky-High Success with Epiphan Pearl: Revolutionizing Remote – Videoguys

Small Company, Big Impact in Video Production
Talon AV, a video production company, excels in providing top-notch video streaming, recording, and production services for live events. From corporate webinars to multi-day conferences with multiple breakout rooms, their efficiency enables them to manage multiple concurrent events, making a significant impact despite being a small team.
How Talon AV Manages Remote Event Production with Epiphan Pearl
To overcome the challenge of being in multiple places simultaneously, Talon AV’s CEO, Tim Kerbavaz, turned to Epiphan’s Pearl systems. These systems are renowned for their flexibility, reliability, and, most importantly, remote control capabilities. By deploying Pearl systems on-site and connecting them to the network, Talon AV can oversee multiple events from any location. Remarkably, they have even managed live streaming sessions from an airplane. This is all made possible through Epiphan Edge™, which facilitates remote production and monitoring of Pearl systems from anywhere.
Scaling Operations with Remote Event Support
The ability to manage multiple devices remotely has allowed Talon AV to expand its services beyond a single site. They now offer remote event support services, enabling the team to handle several events simultaneously. This scalability has significantly boosted their operations without the need for a larger physical footprint.
Key Benefits of Using Epiphan Pearl and Edge for Remote Event Management
-
Remote Management: With Epiphan Edge, Talon AV can remotely monitor and control Pearl devices, make real-time adjustments, and manage file workflows from various locations. This capability is a game-changer for events spanning multiple rooms or locations.
-
Versatile Streaming and Recording: Pearl’s adaptability ensures high-quality video delivery under different network conditions and requirements. Whether it’s direct streaming or point-to-point SRT links, Talon AV can handle diverse show needs with one set of hardware.
-
Large-Scale Event Management: For events with multiple breakout rooms, Pearl hardware facilitates efficient management and recording. It meets strict security requirements while maintaining a compact operational footprint, proving indispensable for capturing content in large-scale events.
Conclusion: Talon AV’s Success Story with Epiphan Pearl
For Talon AV, Epiphan’s Pearl and Edge are indispensable tools in their event production arsenal. These products have enabled Tim and his team to tackle the challenges of live event production head-on. The reliability and flexibility of Epiphan products have not only streamlined Talon AV’s operations but also significantly boosted the company’s image.
By managing more clients and multiple events simultaneously, Talon AV has set itself apart in the industry. Their ability to achieve more with fewer resources has enhanced their reputation for efficiency and excellence, making every event a success story.
Explore how Epiphan Pearl and Epiphan Edge can revolutionize your remote event production, just like they did for Talon AV.
Citizen Sleeper 2: Starward Vector Preview – On The Run, Again – Game Informer
Citizen Sleeper took me by surprise in 2022, giving me a rare new video game experience, both mechanically and narratively, and my dice-centric role-playing adventure has stuck with me since. I still think about my Sleeper and what they’re up to now. In a year where Elden Ring didn’t release, it would have been my game of the year with a bullet – read my Citizen Sleeper review here to find out why. Now, a little more than two years later, I’ve played parts of the opening hour of Citizen Sleeper 2: Starward Vector and find myself desperate to play more. It brings back its incredible sci-fi score, cyberpunk (yet distinct) visual style, and thought-provoking and stress-inducing writing. It infuses everything I love about the first Citizen Sleeper with new mechanics that fuel the game’s central decision-making processes.
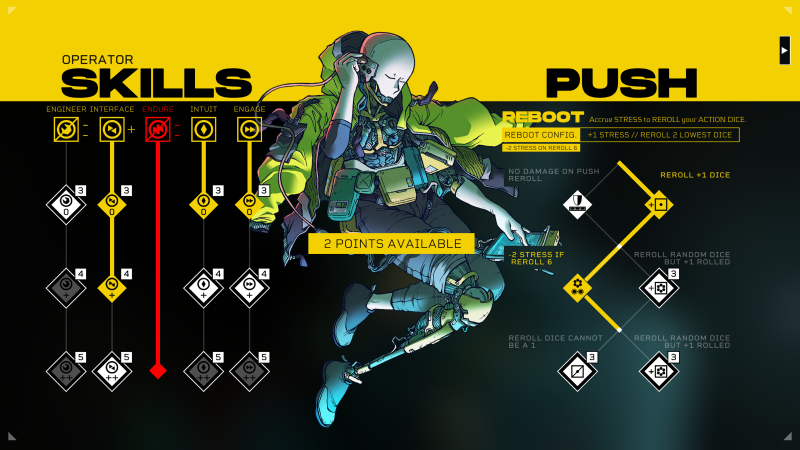
Like the first game, I assign my Sleeper one of three classes. I go with the Operator, which the game describes as physically fragile but great at working in interfaces and computer systems. Immediately, I notice the selected class plays a more significant role in how your experience will play out because the Operator lacks access to an entire skill. This means I’m automatically at a disadvantage with any action requiring said skill. However, I have access to the Reboot skill that allows me to reset my system, which mechanically means I gain a dice reroll. It’s a risky skill, as I could roll an even lower number, putting whatever action is at hand further into jeopardy. I could also roll a significantly better number, too, though.
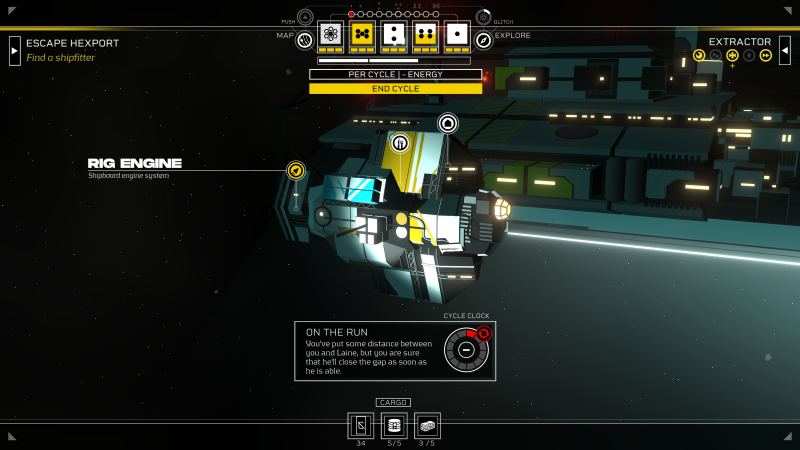
The story picks up after my Sleeper has been helped by their friend Serafin. I’ve recently rebooted my entire system, ending my dependence on the Stabilizer drug that plays a major role in Citizen Sleeper and the gang leader Laine, who supplies it to me. It’s these types of touchstones to the first game players will find in the sequel, which is its own standalone story. However, the reboot was just a partial success. Sure, I no longer need Stabilizer, but my artificial body is malfunctioning. Serafin and I flee on a ship called the Rig, which we steal from Laine and take to Hexport.
Laine, unhappy with everything we’ve done, is after us by way of gang members, bounties, and more. He’s someone my Sleeper once saw as a protector, a savior even, but now, they know him as “a pursuer, a tormentor, a nightmare.” I can’t help but notice the setup for Citizen Sleeper 2 is nearly identical to the first game – a Sleeper whose body is fighting against them is on the run from someone bigger than them. Gareth Damian Martin, the sole developer at one-person studio Jump Over The Age (though Martin has some help in developing Citizen Sleeper 2), says that’s intentional.
“I’m a big fan of noir storytelling,” Martin tells me. “I guess it’s a bit of old-fashioned storytelling, but I like the idea about an ordinary person who’s getting sucked into extraordinary circumstances trying to improvise their way through it.”
They say they wanted to change it up a bit for the sequel – instead of running from a corporate conglomerate, you’re running from a singular person and his gang of underlings. Martin says they feel the result is a story that’s a “bit more intimate and intimidating, and in a way, weirdly scarier because it feels a little more dangerous.”

Laine
After selecting my Sleeper, I’m thrown right into the dice action that returns from the first game. Serafin is going to check on something, so they task me with going to the Hexport Docks to pick up some small gigs. I put a 5-dice (the higher the number, the more likely the action I assign the dice to ends up with a positive outcome versus a neutral or costly negative one) on a “Chat to Crews” function here to get some tips on potential crew recruits and contacts. However, despite the high positive chance with a 5-dice, I get a neutral outcome and only get material. From here, I explore the area more and eventually unveil a new location after completing enough actions at a different spot. It’s “The Bends,” and I can gamble some Cryo (currency) in the Star and Stoker game or buy some fries to restore my energy.
You lose one segment from your energy bar for each cycle or day of action (largely determined by your running out of dice). If this bar is empty, you starve and gain one stress bar per cycle. It’s here I learn Martin has taken a recurring feeling from the first game – the stress one experiences while playing and its effect on your decision-making – and turned it into an actual in-game mechanic aptly named stress. This dictates how much damage your dice will take when rolled. Damage a dice three times, and it breaks until it’s fixed.
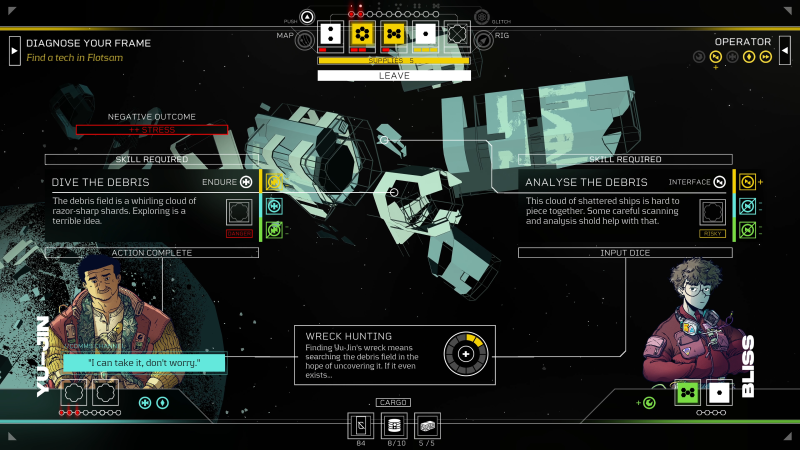
Stress joins another new mechanic called Glitch, which I don’t experience in my hands-on demo but witness in a hands-off preview played by Martin. If you roll your dice while you have some Glitch, which, like Stress, is represented in the U.I., you can roll Glitch dice. These have an 80% chance for a negative outcome but a 20% chance for the best possible outcome, once more playing into the risk-and-reward feel permeating the game. You gain Glitch based on how you repair or heal your body – scrap parts might yield more Glitch, whereas more premium resources yield little to none. Together, these mechanics add an exciting but stressful new layer to each decision you make with dice.
“When you look up there [at your U.I. bar], there’s this kind of game of plates spinning,” Martin tells me. “The big part of those plates is actually you dealing with the facilities and capabilities of your body. Even when you heal one of your dice slots, you’re having to deal with the fact that you’re taking on Glitch, and therefore, you’ve got to think about, ‘Do I go on a job right now when I’ve got this level of Glitch or do I rest a bit?’ In general, this is connected to me adding a bit more mechanical heft to the game, especially when it comes to players who aren’t necessarily drawn to the role-playing without some kind of mechanical support for that.”
Martin hopes these additional layers of mechanics provide new pathways for role-playing. With Citizen Sleeper, they noticed some players would lean into the role-playing aspect, making money and decisions based on how their Sleeper might. However, some players said, “I like to make money wherever I make the most money.” It was strictly mechanical for them.
“I always felt like, ‘Oh, that’s a shame because I want you to engage with this character that you’re playing and the story they’re telling,’ so this time around, if I want players to think about how they have to deal with something, there’s a mechanical effect,” Martin says.
As there’s no point in spoiling the narrative events that transpire in this preview build, given how narrative-focused the series is, I’m going to jump ahead to another new mechanic: Contracts. After picking one up at the Hexport contract board, I learn these high-risk, high-reward jobs greatly expand the scope of Citizen Sleeper 2. Unlike the first game, which primarily takes place on a singular space station called the Eye, Citizen Sleeper 2 gives players access to a large star map with various points of interest.
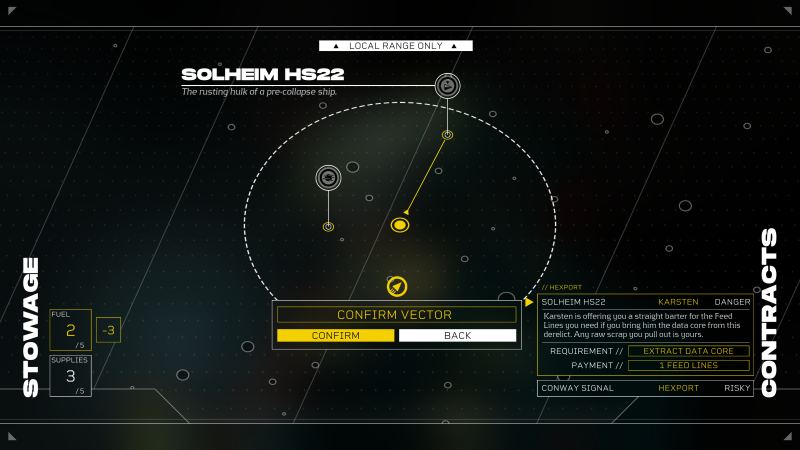
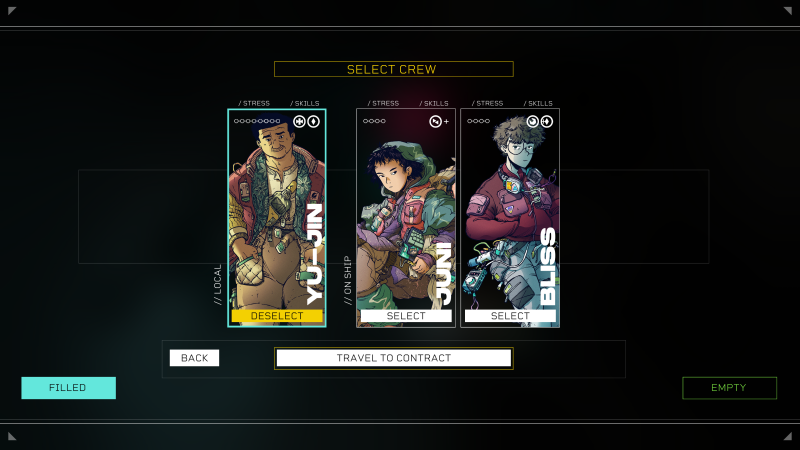
Before embarking on this contract, the game warns me to ensure I have enough fuel to travel to the contract, supplies to keep my Sleeper and crew going, and that I take the opportunity to scout out new freelance crew members to join. Your crew plays a significant role both in the main narrative of Citizen Sleeper 2 and these contracts, which Martin describes as vignettes or episodes inspired by, for example, sub-arcs in series like Firefly, Cowboy Bebop, or other sci-fi greats. They say you might do two or three contracts and see the same character repeatedly, or there might be contracts where you meet a character for the first and last time. Regardless, it’s about the “little story” you get from these contracts. Some are high intensity, others are more laid back, Martin says. The one I do in my preview falls into the former.
After traversing across space to a security drone with something inside I need, I learn that said drone is rigged to blow. Four mistakes and the contract could be over on account of an explosion. As such, I must disable parts of the drone in a semi-sequential order while maintaining a balancing act of dice, supplies (and energy), and more. Supplies, of which I can carry a maximum of five at this point and do before leaving for this contract, automatically replenish energy after each cycle during a contract. When you run out of supplies, your energy will deplete each cycle, and as your energy depletes, your dice get worse, jeopardizing the mission at hand. That’s why preparing ahead of time for a contract is essential.
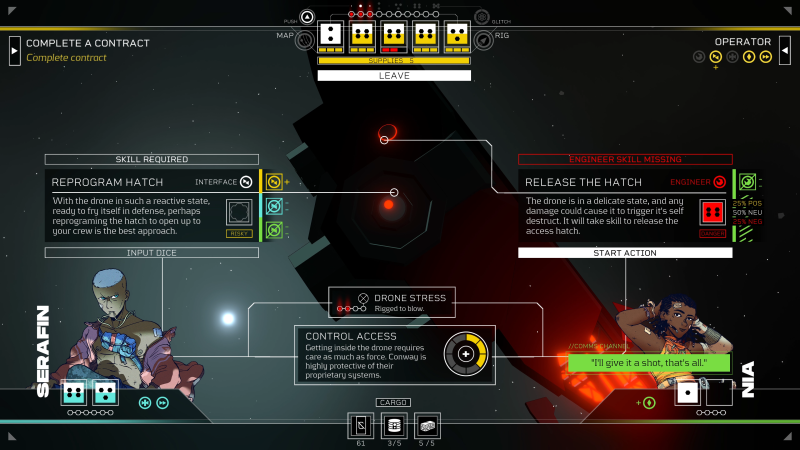
However, with a drone rigged to blow after four mistakes, I can’t risk using low-number dice with high chances of failure or my low-number crew dice, which, like mine, take into effect our skill proficiencies and can be used alongside my own Sleeper’s dice. Not wanting to risk the low-number dice, I end cycles prematurely, crossing my fingers that I roll some higher-number dice the next day. Fortunately, I do and complete the contract. Some intriguing story stuff happens when I return to Hexport that I won’t spoil here, and my demo is over.
During the preview Martin plays, I see even more of the mechanical and narrative synergy (and stress) of Citizen Sleeper 2 at play. You can utilize Push to get dice bonuses, but doing so immediately adds to your Stress meter. The skill tree is more expansive and customizable, designed with freedom in mind rather than guiding players toward a specific build. Everything I see excites me.
Martin says they’re halfway through developing the game and already at 120,000 words – Citizen Sleeper and its DLC totals 180,000 words, promising a rich storytelling experience in the sequel. There’s a larger push from Martin to lean into Citizen Sleeper’s tabletop inspirations and its cyberpunk themes. Citizen Sleeper 2 is, on paper, a classic example of more story, more systems, more to do. But critically, Martin isn’t just going bigger, instead carefully curating an experience that strikes sharply at the heart of what made the first game work so well: the oh-so-fine balance between success and failure and the stress that lives between the two. If the heart-pumping I felt during my hour with the game is any indication, Martin has rolled a strong set of dice in this first preview cycle for this sequel.
