Elon Musk has initiated legal action against OpenAI and its CEO Sam Altman, alleging a departure from the…
Two BTR-80s Exploded at the Exact Same Time – What Hit Them? – Technology Org
A pair of Russian BTR-80 eight-wheeled armoured personnel carriers rushed together to storm Ukrainian positions and blew up…
Weekly News for Designers № 732 – JavaScript Bloat in 2024, Figma for Developers, New CSS UI Kit
A Web Designer’s Accessibility Advocacy Toolkit
A toolkit for web designers to advocate for accessibility and offer strategies and tips to improve web interfaces for all users.
JavaScript Bloat in 2024
Nikita Prokopov discusses the excessive use of JavaScript on websites and calls for a focus on leaner, performance-oriented web development.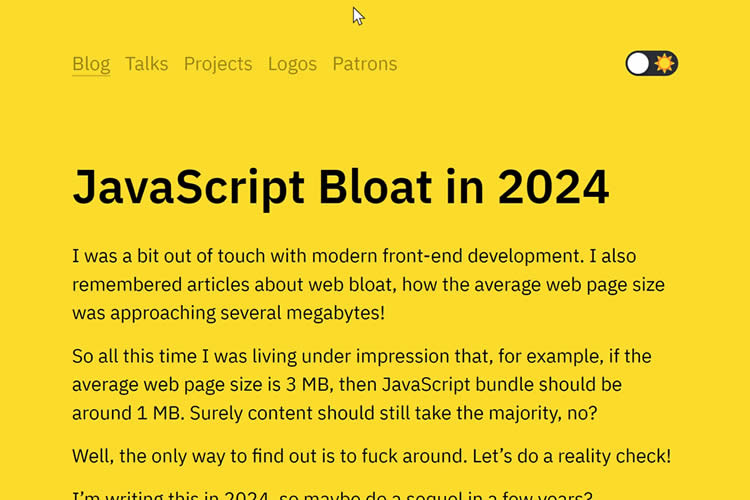
Mastering Figma for Developers
This guide highlights Figma’s advantages for developers, such as its collaborative, cloud-based platform, and tools that streamline design-to-development workflows.
Tailframes CSS UI Kit
A new UI kit for Tailwind CSS, offering pre-designed components to speed up web development with easy customization and a focus on productivity.
Slideshow Templates for Premiere Pro
Explore top slideshow templates for Premiere Pro to make your presentations stand out. Perfect for any project, these templates offer creative solutions.
A Deep Dive into Aptos
An insightful exploration of Microsoft’s new default font, Aptos, detailing its commitment to inclusivity, accessibility, and adaptability in design.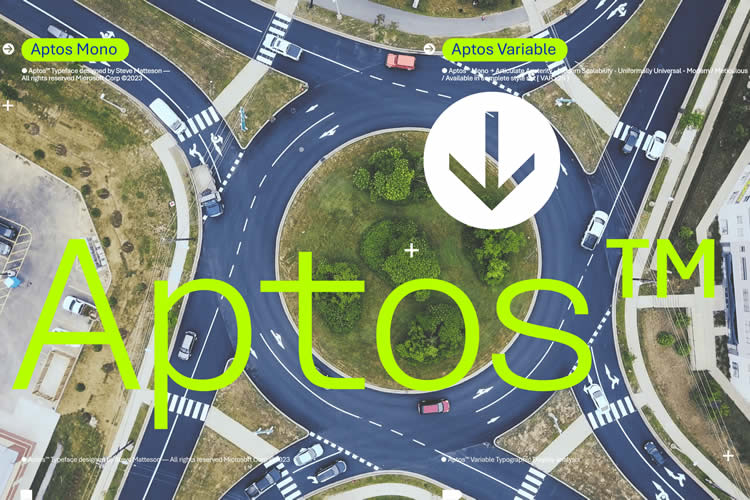
Winduum CSS Component Framework
A new modular CSS component framework built on top of TailwindCSS, emphasizing modern CSS features for building accessible, customizable, and lightweight web components.
Product Design is Overtaking UX 
Create & Manage Block Patterns in WordPress
WordPress now has a way to create, manage, and share block patterns – all from within the Block Editor. Learn how it all works.
How Jakob Nielsen Developed the 10 Usability Heuristics 
Making of True Multi-Brand Design System
A detailed journey into building a single design system for multiple brands, platforms, or products.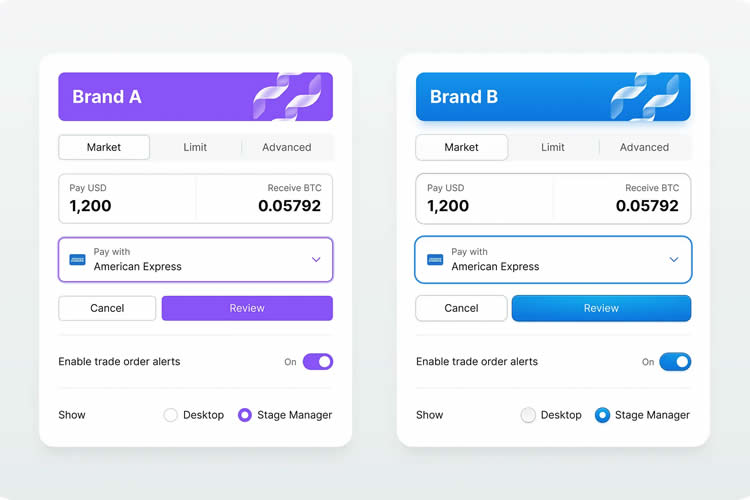
Free Responsive Icons
A collection 0f 266 icons for UI design. In Figma and Skecth formats.
Exploring 3D Effects with 2D Optical Illusions
Learn how to create 3D effects with 2D optical illusions using CSS, JavaScript, and GSAP, focusing on perspective manipulation and staggered animations for realism.
Cheap Drones Defeat Even The Most Modern Russian Tanks – Technology Org
In the Donetsk region, the Ukrainians destroyed something impressive. It turns out, the pride of the Russian armoured…
Revolutionizing Delivery Efficiency with Advanced Route Planning Technology – Technology Org
Are your delivery routes as efficient as they could be? It’s a question that can keep any logistics…
Map Your Way to Money: Creative Use of Google Maps for Extra Earnings – Technology Org
Imagine you’re Googling for a new café, shop or even a plumbing service to visit in your area….
Pokémon Day 2024, Penny’s Big Breakaway Impressions | All Things Nintendo

This week on All Things Nintendo, Brian starts by providing an update on the future of All Things Nintendo. Game Informer’s Kyle Hilliard then joins him to break down all the news of Pokémon Day 2024 before they round out the show with Brian giving his hands-on impressions of the next game from the Sonic Mania developers, Penny’s Big Breakaway.
[embedded content]
If you’d like to follow Brian on social media, you can do so on his Instagram/Threads @BrianPShea or Twitter @BrianPShea. You can follow Kyle on Twitter: @KyleMHilliard and BlueSky: @KyleHilliard.
The All Things Nintendo podcast is a weekly show where we celebrate, discuss, and break down all the latest games, news, and announcements from the industry’s most recognizable name. Each week, Brian is joined by different guests to talk about what’s happening in the world of Nintendo. Along the way, they’ll share personal stories, uncover hidden gems in the eShop, and even look back on the classics we all grew up with. A new episode hits every Friday!
Be sure to subscribe to All Things Nintendo on your favorite podcast platform. The show is available on Apple Podcasts, Spotify, Google Podcasts, and YouTube.
00:00:00 – Introduction
00:00:41 – Game Informer Layoff/Future of ATN
00:10:20 – Hi-Fi Rush Switch 2 Rumor
00:14:21 – Arkham Knight Still a Mess on Switch
00:19:39 – Sega Acknowledges Launching Sonic Superstars at Wrong Time
00:28:57 – TMNT Arcade: Wrath of the Mutants Announced
00:34:22 – Pokémon Day 2024 Recap
00:51:53 – Penny’s Big Breakaway Impressions
If you’d like to get in touch with the All Things Nintendo podcast, you can email AllThingsNintendo@GameInformer.com, messaging Brian on Instagram (@BrianPShea), or by joining the official Game Informer Discord server. You can do that by linking your Discord account to your Twitch account and subscribing to the Game Informer Twitch channel. From there, find the All Things Nintendo channel under “Community Spaces.”
For Game Informer’s other podcast, be sure to check out The Game Informer Show with hosts Alex Van Aken, Marcus Stewart, and Kyle Hilliard, which covers the weekly happenings of the video game industry!
Video Generation AI: Exploring OpenAI’s Groundbreaking Sora Model
OpenAI unveiled its latest AI creation – Sora, a revolutionary text-to-video generator capable of producing high-fidelity, coherent videos up to 1 minute long from simple text prompts. Sora represents a massive leap forward in generative video AI, with capabilities far surpassing previous state-of-the-art models. In this…

