In a game of inches, communication service providers (CSPs) are looking for tools or practices to help them get ahead. With revenue in the communications services market projected to reach $337 billion in 2024, there’s inevitably a lot at stake. To explore how CSPs can gain…
Carolyn Harvey, Chief Operations Officer at LXT – Interview Series
Carolyn Harvey has extensive experience leading and growing global operations in the field of search relevance ranking and annotation for ML data. Carolyn is currently Chief Operations Officer (COO) of LXT where she leads the company’s global operations division, ensuring consistent delivery of all AI data programs…
Must-know network security management insights (2024) – CyberTalk

EXECUTIVE SUMMARY:
Network security management refers to the processes and systems that administrators put into place for the purpose of overseeing, regulating and safeguarding an organization’s network infrastructure.
A network security management strategy protects the heart of an organization – keeping employees productive, products competitive and the business resilient, even as disaster strikes.
Amidst a scattershot matrix of users, devices, locations and applications, all operating in a tempestuous threat landscape, how comprehensive (and effective) is your network security management strategy? Could your organization level-up?
Network security management
Discover essential elements of an effective network security management strategy right here. Get actionable recommendations designed to help elevate your organization’s security posture. Be ready for whatever comes next.
1. Establish a network security management framework. Organizations often create ad-hoc network security management strategies, resulting in vulnerabilities.
Recommendation: Avoid this. Establish a clear means of managing network security – from roles to resources. Ensure alignment with other strategy elements, as outlined below. Create a cohesive and comprehensive approach.
2. Identify all network assets. For a network security management strategy to work, it has to include absolutely everything on the network, accounting for the risks associated with all resources.
Recommendation: Maintain a comprehensive inventory of network resources and regularly update it, as to include new devices, applications and services.
3. Analyze points of concern. After identifying network resources, identify more expansive infrastructure risks that could compromise network integrity.
Recommendation: Employ threat modeling techniques to find and evaluate infrastructure risks. Prioritize security efforts based on high-impact areas and scenarios.
In addition, collaborate with cross-functional teams (ex. IT and legal) in order to ensure that all points of concern are addressed in a holistic and comprehensive way.
4. Establish network security policies. The right network security policies can substantially enhance an organization’s cyber security posture.
Recommendation: Create policies that address specific risks associated with your organization’s assets – ex. servers, endpoints and IoT devices.
In addition, ensure that network security policies remain in compliance with relevant cyber security guidelines. Conduct periodic policy reviews to ensure alignment with the latest frameworks, standards and regulations.
5. Adopt a robust authentication and authorization framework. Advanced identity authentication mechanisms render it more difficult for hackers to gain unauthorized access to resources. In this day in age, advanced auth is a no-brainer.
Recommendation: Re-enforce your enterprise security with multi-factor authentication (MFA), role-based access controls and zero trust.
6. Perform regular network audits. Network audits can reveal misconfigurations, compliance gaps and general vulnerabilities. They provide a snapshot of the network’s security posture, helping organizations sidestep major potential pain points.
Recommendation: Create a recurring audit schedule (quarterly or annually) for assessing network components. In your assessment process, leverage automated tools. After audit completion, document your findings, plan remediations, and track progress.
7. Focus on firewalls. Your organization’s firewalls need to deliver.
Recommendation: Redesign existing gateways. Opt for high-performing firewalls that provide AI-powered threat prevention. Ensure that your organization can block both known and unknown threats.
8. Adopt a centralized network management solution. Centralized network management allows for extensive visibility into a wide range of threats across your ecosystem.
Whether you’re in the cloud, the data center or both, centralized management also allows for comprehensive threat detection and simplified compliance.
Recommendation: In essence, centralized network management provides superior protection (as compared to a trove of point solutions) and ensures a stronger security posture. Find a reputable vendor and apply a centralized network management solution.
9. Ensure the resilience of network security. CISOs and cyber security leaders need to design networks with redundancies and failover mechanisms – at all levels.
On product release day, when your organization suddenly sees website traffic spike by 880%, your network needs to be available. When APT 29 attempts to strike, your network should also be available.
Recommendation: Define your network requirements, design the necessary systems, and ensure availability in 99.9% of instances.
It should also be assumed that breaches will occur – update your IR plans so that they prioritize reducing impact and expediting recovery times.
More information
Discover additional forward-thinking network security management insights here. Lastly, subscribe to the CyberTalk.org newsletter for timely stories, cutting-edge analyses and more, delivered straight to your inbox each week.
Elden Ring’s Shadow Of The Erdtree DLC Trailer Promises A June Release Date

After a long wait, we finally have details about Elden Ring’s upcoming DLC, Shadow of the Erdtree. Publisher Bandai Namco and developer From Software released the add-on’s first official trailer this morning which revealed it is launching June 21. Bandai Namco is also releasing a physical version of the game, the Elden Ring: Shadow of the Erdtree Collector’s Edition, which includes a statue and other goodies.
You can check out the trailer below.
[embedded content]
The trailer begins by focusing on a setting where an optional boss appeared in the main game and where you can find Miquella’s egg. The trailer shows new monsters and bosses, like a lion creature with a rotating head and another made entirely of flames. There are also new abilities, items, and weapons, one of which appears to be a roaring bear’s head. There is also some kind a porcupine alligator creature and the player character sprouted angel wings in one fight. Those are just a few of the standout reveals.
The game’s official product page does confirm a few additional details, like the name of the main boss seems to be Mesmer the Impaler. Shadow of the Erdtree is also not standalone despite carrying a $39.99 price tag. The page refers to it as an expansion and it will require the base game. Here’s the official description.
Follow the link to read Game Informer’s Elden Ring review.
Pentiment Arrives On Switch Tomorrow

During today’s Nintendo Direct: Partner Showcase, we learned Grounded is coming to Switch this April, but that’s not the only Obsidian-developed title fans can expect. Blending the adventure genre with a gorgeous storybook aesthetic, Pentiment was a critical darling when it launched on Xbox Series X/S, Xbox One, and PC in 2022. Now, a new stable of players will have the chance to experience the title, as it is coming to Switch tomorrow.
Pentiment puts you in control of Andreas Maler, a 16th-century artist from Nuremberg who finds himself in the middle of several murder mysteries. Taking place over the course of 25 years, you must investigate the murders, collect physical proof, interview townsfolk, and accuse who you think committed the crime based on the evidence you gather.
When it launched on Xbox in PC, Pentiment earned an 86 on reviews aggregate sites Metacritic and OpenCritic. Game Informer‘s Charles Harte felt similarly, awarding it an 8.5 out of 10, saying Pentiment is “a perfect example of this, telling a deep, complex story about religion, truth, and history in the form of a book, which the player experiences as it’s being written. Despite a few sections with inconsistent pacing, it’s a must-play for fans of adventure games.”
Pentiment arrives on Nintendo Switch tomorrow, February 22. For more on the title, be sure to check out our review here. Pentiment joins Grounded as previous Xbox exclusives to come to Switch. According to Xbox’s Phil Spencer, there are four games in total that will arrive on additional platforms in the near future. The other two are reportedly Sea of Thieves and Hi-Fi Rush, but neither was featured on today’s Nintendo Direct: Partner Showcase.
Weekly News for Designers № 730 – Design Pattern Guidelines, Aesthetics vs. Functionality, CSS Variables Generator
Design Pattern Guidelines
Here’s a comprehensive guide to design patterns, including a collection of resources for various interface elements like forms, navigation, and controls.
Opportunities for AI in Accessibility
Aaron Gustafson discusses how artificial intelligence could enhance accessibility and explores the potential benefits.
Aesthetics vs. Functionality
This article explores the balance between aesthetics and functionality in UX design, highlighting the importance of both in creating effective digital products.
Universal Resume System
This is a flexible resume layout system for Figma that has been inspired by the design work of Dieter Rams.
Sora Text-to-Video AI
OpenAI’s new AI model that creates videos from text, producing up to one-minute high-quality videos from user prompts.
Monospaced Fonts for Coding
We share the best free fonts for coding and programming and also offer some pointers for selecting your perfect monospaced font.
High Definition CSS Color Guide
A detailed guide that introduces CSS Color Level 4, expanding web color capabilities with wider gamuts, more colors, and advanced gradients, enhancing visual richness and fidelity in web design.
Creating the Perfect Icon
This article outlines steps for creating impactful icons, focusing on their recognizability, consistency, and clarity.
Design Trends 2024
Discover the potential design trends of this year, like surrealism in 3D, AI-generated art, holographic design, and minimalism and brutalism.
25 Years of Freelancing
Eric shares some valuable lessons from his 25 years as a freelance web designers. Things that will help you on your own freelance journey.
On-Scroll Animation Ideas
Codrops shares some innovative ideas for animating sticky sections as they leave the viewport.
How to Favicon in 2024
Here’s a guide on simplifying your favicon setup by just using six files. It also includes practical steps for implementation.
CSS Variables Generator for Figma
Improve your design-to-development workflow by instantly converting Figma variables and styles into CSS custom properties.
Guide To Designing For Children
A guide on designing digital products for children aged 3-12. Covering user behavior insights, considerations for parents, and practical UX guidelines.
Fun Examples of SVG Shape Usage in Web Design

Scalable Vector Graphics (SVG) make for versatile design elements. They can be intricate or simplistic. You can combine them with animation and special effects. And they’re inherently responsive.
It’s no wonder that web designers have taken to the format. SVG adds a new level of flexibility compared to pixel-based images. They are a perfect match for modern design. Plus, browser support is universal.
As such, we went on a search for examples of SVG shapes. The goal was to find a diverse collection of implementations. Curious about what’s possible? Take a look at these eight fun examples of SVG shapes in action.
Simple CSS Waves by Goodkatz
Divider graphics are a natural fit for the SVG format. These images stay razor-sharp on every screen. The animated waves in this snippet add a touch of elegance. Even better, mobile users can enjoy the feature without a performance hit.
See the Pen Simple CSS Waves | Mobile &Full width by Goodkatz
SVG Image Unveiled by Silvia Gioia Florio
Here’s an example of what SVG masking effects can do. Watch as polygons fall from this tree to reveal a masked image. CSS and JavaScript are used to power the animation. This effect used to require the likes of Photoshop and Flash. No need for those heavy tools anymore.
See the Pen SVG Image Unveiled by Silvia Gioia Florio
SVG Shape Page Transitions by Pixelbuilders
We can use SVG to create compelling page transitions. Click the “hamburger” menu or scroll to unleash a drip effect. It’s as if the screen is melting right before our eyes. And it’s sure to grab a user’s attention.
See the Pen SVG Shape Page transitions by Pixelbuilders
Liquid UI Elements by Aaron Iker
Mundane elements like radio buttons and checkboxes also benefit from SVG. This snippet features common form elements dressed up with slick animations. It adds a highly-polished look that is miles ahead of the default.
See the Pen Liquid UI Elements by Aaron Iker
SVG Flowers Login Screen by Meg Wayne
SVG doesn’t have to be the centerpiece of an element. It can also flourish in a decorative role. Here, a single shape is repeated and styled via CSS. Each variation creates depth and beauty.
See the Pen SVG Flowers Login Screen by Meg Wayne
SVG Adaptive Gradient by Andros Guiradó
This snippet uses SVG filter effects to create a noisy gradient. The animated waves stretch across the viewport. It might be a neat addition to a footer area.
See the Pen SVG adaptive gradient by Andros Guiradó
There are a few implementations of SVG in this snippet. But our primary focus is the curved background. It’s a key element in the presentation. The added text and video combine to create a jaw-dropping effect.
See the Pen Blend-Mode Sticky Nav &Hero by Jalin Burton
SVG Animated Drum Kit by Josh
Let’s finish this collection with a bang. Don’t have a drum kit handy? You can always play this virtual set. SVG is used to power the graphics. Meanwhile, some spot-on sounds bring them to life. Here we go, Ringo!
See the Pen SVG Animated Drum Kit (Play Me!) by Josh
Adding Shape to Your Design
SVG has become a staple of web design. The format comes with plenty of advantages. And we can use it to create effects that used to require hacks.
All told SVG is among the most powerful tools we have. It adds a world of possibilities for design, movement, and interactivity. What’s not to love?
Check out our CodePen collection for even more examples of SVG shapes. You might find the perfect use case for your next project.
Related Topics
Top
Everything Announced At Today’s Nintendo Direct: Partner Showcase
Today’s Nintendo Direct: Partner Showcase has come and gone, and the presentation revealed a number of third-party announcements and several release dates for previously known games coming to Switch. If you don’t feel like sitting through the 25-minute presentation, here’s a quick summary of the event’s notable updates.

Grounded And Pentiment Come To Switch
Two of the four mysterious Xbox titles coming to other consoles were revealed, both from Obsidian Entertainment. Grounded comes to Switch on April 16, while Pentiment arrives tomorrow, February 22.

Ender Magnolia: Bloom in the Mist – Summer 2024
Set within the world of Ender Lilies: Quietus of the Knight, the game sees characters defeating and teaming with deadly homunculi to rescue a devastated world.

Arranger: A Role-Puzzling Adventure – Summer 2024
Set in an interconnected puzzle world, you’ll navigate on a grid where everything moves when you move. You’ll take down monsters, help townfolk, and, of course, solve puzzles.

Unicorn Overlord Gets A Demo Today
We’ve seen a lot of VanillaWare’s beautiful turn-based strategy game, but now we can finally play it ahead of its March 8 release.

Monster Hunter Stories – Summer 2024
The 2017 Nintendo 3DS RPG spin-off of Monster Hunter is heading to Switch (as well as PlayStation 4 and Steam). In addition to HD visuals, this port includes new voiceovers, a museum mode, and additional content previously only available in Japan.

Disney Epic Mickey: Rebrushed – 2024
2011’s Epic Mickey is getting touched up for a comeback on Switch. The enhanced remake includes updated graphics, new skills for Mickey, and other improvements. You can learn more here.

Shin Megami Tensei V: Vengeance – June 21
This definitive version of SMT V includes the base adventure along with a new storyline featuring new locations and demons.

Star Wars: Battlefront Classic Collection – March 14
The original Battlefront games have been remastered and updated with features such as new playable characters Kit Fisto and Asajj Ventress and bonus maps Jabba’s Palace, Bespin: Cloud City, and Yavin 4: Arena.

Sword Art Online Fractured Daydream – 2024
Either alone or with a friend in co-op, you’ll tackle a distorted version of Sword Art Online that includes battling in 20-player raids against powerful enemies.

Gundam Breaker 4 – 2024
Build your own Gundam, blow up other mechs, take their parts for your own ,and repeat. For Gunpla fans, the real thrill is assembling your own suits with parts from 250 base kits to take into battle or show off to others.

Super Monkey Ball Banana Rumble – June 25
Sega revealed a brand-new Super Monkey Ball game featuring 200 fresh courses, 16-player multiplayer, and new moves for AiAi and friends. You can learn more here.

World of Goo 2 – May 23 console exclusive
The long-awaited sequel comes to Switch first as a console exclusive this May

Fantasy Life i: The Girl Who Steals Time – October 10
The Fantasy Life series gets a new chapter in which you can assume 14 different roles called Lives to build a town in the present and explore an island in the past to solve mysteries. You can also play in four-player co-op.

Another Crab’s Treasure – April 25
As a hermit crab who’s lost its shell, you’re on an adventure to reclaim it. This involves using any piece of trash in a polluted ocean as a temporary shell, each with different abilities, to defend or attack underwater threats.

Penny’s Big Breakaway – Out today!
This throwback 3D platformer from the makers of Sonic Mania is out now! You can learn more here.
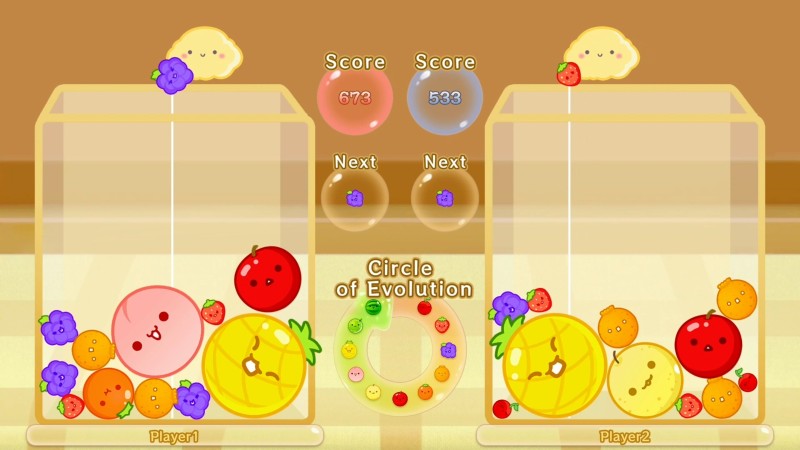
Suika Game Multiplayer Mode Expansion
The adorable (and hard to put down) fruit-matching game gets paid DLC that adds a local 2-player battle mode, and the eventual addition of online multiplayer. Time Limit and Attack modes join the base game’s offerings.

Pepper Grinder – March 28, Demo Out Today
The drill-centric platformer looks great and, if you checked out its recent Steam Next Fest demo, plays just as good. It’s got a release date and a free demo for Switch players to enjoy.

Pocket Card Jockey: Ride On! – Out On Switch Today
The formerly iOS-exclusive sequel to Pocket Card Jockey is coming back home to a Nintendo console

Contra: Operation Galuga – March 12, Demo Out Now
This modern reimagining of the original NES Contra, which features six playable characters, now has a release date.

Rare games on Switch Online
A bundle of classic Rare games come to Nintendo Switch Online: Snake Rattle ‘N’ Roll, R.C. Pro-Am, Battletoads in Battlemaniacs, Killer Instinct, and Blast Corps. Learn more here.

Endless Ocean Luminous – May 2
This new Endless Ocean title plunges players into an everchanging open ocean. You can dive alone or alongside up to 30 players online, where you’ll encounter 500 species of marine life, including extinct creatures.
Additionally, here are some quick hits:
Snufkin: Melody of Moominvalley – March 7
Demon Slayer – Kimestsu no Yaiba – Sweep the Board! – April 26
Kingdom Come: Deliverance – Royal Edition – March 15
Skull and Bones Review – Middle High Sea – Game Informer

Like a ship that has changed tack countless times and delayed its arrival at port, Skull and Bones has launched far later than expected and faced trouble along the way. Even so, this pirate adventure surprised me with the breadth of its world, the richness of its commerce simulation, and an approachable and rewarding naval combat system. As a living game built around seasonal content and a growing universe, it has a ways to go to be at its best, but the bones of a quality experience are here.
You are a treasure-hungry pirate eager for infamy as you set out across the Indian Ocean, tracking down treasure chests, plundering seaside towns, and, most prominently, battling other ships on the high seas. On-foot activity is reserved for social spaces and the most minimal of story development – the entirety of action unfolds on the water, where you develop an impressive array of ships and weaponry through your ill-gotten gains.
Launching where the maritime voyages of the Assassin’s Creed games left off, I enjoyed the deliberate pacing of sea exploration and movement, punctuated by the regular interruption of cannon fire and mortars. Especially in the early hours, I was often transfixed by the sights and sounds of moving across the water, listening to my crew’s sea shanties, watching for breaching whales, and using my spyglass to spot distant shipwrecks. It’s a big and beautifully crafted world of island-rich open waters and tricky narrow riverways.
Combat has just enough complexity to remain entertaining as you balance turning speed, facing, and aiming to maximize damage output while dodging or bracing against the worst attacks of your opponents. The real fun comes from building and tweaking your boat as an engine of destruction; the variety of ship builds and approaches to fighting kept me consistently interested in chasing that next upgrade. I appreciated the approach to tracking specific items and upgrades, with clear markings on the map for where to find what you want. Because of that, it becomes about whether you have enough money to buy something or a powerful enough ship to take it.
The bulk of play is PvE encounters against privateers, merchants, and corporation ships, played either solo or cooperatively. Even if the open servers allow for both structured and informal PvP, my anecdotal experience was that most players were focused on their own adventures. If they joined a battle, it was often to help out. Your mileage may vary, but I liked the mix of mostly campaign-style progression with the option to connect with other players when I wanted.
[embedded content]
Beyond ramming and blowing up other ships, Skull and Bones’ other core pillar is commerce. Ubisoft has built a robust trading system, the most lucrative of which involves illicit rum and opium shipments. I appreciated how the game allows players to choose how much they want to engage here. The selling of commodities gathered from sunken ships is the most superficial layer, but you can also run your own manufacturing and delivery contracts for higher sums. And as you round the corner into the endgame, an entire kingpin empire opens up, letting you take over lumberyards and other factories to generate income passively.
The pirate life eventually wears out its welcome; many of the game’s most significant problems only arise after many hours of play. While it’s fun in the early hours getting your bearings in an unfamiliar sea, later side and main missions become painfully repetitive. Long ocean voyages start to lose their charm, and a fast travel system that only works from port feels increasingly restrictive since you’re often eager to return to a mission giver to keep the action moving.
The freeform progression that was so welcome in the early hours also causes problems over time, as it’s too easy to be over- or under-leveled for certain content you might wish to confront, robbing many encounters of tension since the winning party is so evident from the outset.
The storytelling is incredibly sparse, led by very few core contacts, all of whose arcs are pretty one-note. And while it’s nice that you can customize the look of your pirate captain, their voiceless absence of personality feels especially ill-suited to the big personalities you expect in a classic pirate tale.
Nonetheless, the combination of building a commerce empire, sea monster hunts, engaging in late-game PvE and PvP events, and the chance to continue tweaking and building your ideal pirate ship has appeal even after the core story missions wrap up, giving me hope that longterm endgame could be entertaining. And while it’s early days, I saw potential in the larger ship team-up activities I tried out, where each ship takes on specific roles like you might see in an MMO.
Despite its long and circuitous course to arrive at port, Skull and Bones is the type of game that may change significantly in the coming months. But to evaluate it as it stands, fellow pirate enthusiasts may discover what I did – a flawed but beautifully presented historical fantasy in which one can take to the water and make a fortune, even if absolutely everything about the pirate life isn’t always pretty.